Are you afraid that someone might spy on your WhatsApp conversations? Would you like some advice on how to defend yourself against such threats? Then I think you have come to the right place at the right time.
Given also the numerous requests I received on the subject, today I decided to take care of privacy on WhatsApp: I will tell you some of the main techniques used by attackers to intercept conversations on this very popular messaging service and, most importantly, you I will recommend to take some preventive measures to avoid someone snooping on your account. So, are you ready to get started?
I'll tell you right away: fortunately spying on WhatsApp messages is not as easy as reading (or at least it's not anymore), but woe betide letting your guard down! We should always be careful and follow all those common sense rules that allow us to perform our digital activities in a reasonably calm manner. If you want to understand better what I mean, read on, you will find everything explained below. We will start analyzing all the threats against which we must be on guard and then we will see, together, what measures to take to avoid them. Enjoy the reading!
Sniffing wireless networks

One of the most "popular" spying techniques involves "sniffing" wireless networks with software such as Wireshark (which I also told you about in my tutorial on how to sniff a wireless network). The term "sniffing" indicates a wireless network monitoring activity that allows you to capture all the information that travels in the clear on the latter.
In the case of WhatsApp, an attacker could use sniffing to monitor the network to which the victim's smartphone is connected, but fortunately this technique should no longer work.
In fact, in late 2014, the developers of Open Whisper Systems announced a collaboration with WhatsApp that brought their end-to-end encryption (called TextSecure) inside the famous messaging app. 1
End-to-end (point-to-point) encryption is a technology that allows you to protect information from unauthorized access using a dual-key system: one public and one private. In the specific case of WhatsApp, the public key is shared with the interlocutor and allows outgoing messages to be encrypted. The private key, on the other hand, resides only on each user's smartphone and is used to decrypt incoming messages.
This means that messages leave the sender's phone and reach the recipient, via WhatsApp servers, in encrypted form. The only ones able to decrypt the contents are the owners of the keys used to generate them, i.e. the legitimate senders and recipients.
So, is WhatsApp impregnable? Well not really. End-to-end encryption potentially eliminates tracking techniques, but unfortunately there are other "weapons" that attackers can use. spy on WhatsApp messages.
In addition, we must consider the fact that WhatsApp is a closed source software, that is, it is not possible to analyze in depth the source code, so we can not know if the implementation of end-to-end encryption has been done in a workmanlike manner. or less.
Moral of the story: the situation should be calm enough, but you should not let your guard down.
Identity theft

One of the greatest dangers to our WhatsApp accounts is currently represented by identity theft, that is, from unauthorized access to our conversations through the "trick" of the authentication systems of the service.
Identity theft via WhatsApp Web
One of the easiest ways to steal someone's identity on WhatsApp is to take advantage of the Stay Connected feature of WhatsApp Web, the service that allows you to send and receive WhatsApp messages on your PC using your cell phone as a "bridge".
I also told you about it in my post on how to use WhatsApp on PC: to access WhatsApp Web, simply frame the QR code that appears on your computer screen with your smartphone. After that, if you leave the check mark next to the active item Stay connected, the service works without additional authentication. It is enough that the cell phone on which the original client is installed is connected to the Internet (no matter whether it is on the same Wi-Fi network as the computer or on other networks).
What does this mean? That an attacker could steal your phone with any excuse, frame the WhatsApp Web QR code on your computer (or even on your tablet, using the desktop view mode included in many browsers) and access your messages without you noticing.
Fortunately, there is a solution to overcome this problem: by activating a protection system on your device by using biometric data, such as unlocking the device via face or fingerprint, this system will be required, for confirmation purposes, including access. WhatsApp Web / Desktop.
MAC address cloning
MAC address cloning is another fairly refined technique that attackers can use to steal a user's identity on WhatsApp. It is still quite effective but its complexity, and especially the time needed to implement it, mean that it is not very widespread.
The MAC address is a 12-digit code that uniquely identifies all devices capable of connecting to the Internet. It is also used by WhatsApp to verify the user's identity, so if it is disguised to look the same as that of another phone it can be used to access other people's accounts.
To "clone" a person's MAC address, the attacker on duty must install ad-hoc applications on their smartphone (e.g. BusyBox and Phantom Mac Address for Android, both of which require root). Then he must take over the victim's smartphone, must find out the MAC address (just refer to the Android or iOS Menu Information section) and must set the same code on his phone.
When the operation is completed, the "spy" must install a new copy of WhatsApp on his smartphone, activate it with the victim's number and enter the verification code that arrives on the latter's phone. As mentioned, this is a rather lengthy operation, not within everyone's reach, but it should still be known to avoid unpleasant surprises.
Note: without prior cloning of the MAC address, it is practically impossible to activate WhatsApp with someone else's number. Or rather, it is possible but totally useless. The service, in fact, allows you to use only one smartphone for each phone number and, therefore, the legitimate owner of the account would only need to reactivate the application on his device to "cut the legs" of any spy (which, among other things, would make him be discovered immediately by the victim).
Spyware applications

Another danger to be on guard against are so-called spy-apps, apps that are installed directly on the smartphones of the people to be spied on and hide their presence.
Even parental control apps or anti-theft software can be configured to spy on the user and take screenshots of the smartphone. I told you about it in detail in my tutorial on how to spy on Android phones.
How to defend yourself

At this point you are probably wondering how to protect yourself from all these threats. Well, absolute security does not exist, but if you try to put into practice all the tips I'm about to give you, you should be able to sleep reasonably soundly.
- Always use the most updated version of WhatsApp - WhatsApp developers are constantly working on the security of their software. If you want to sleep relatively soundly, open the store on your smartphone and make sure you're using the latest version of the app.
- Use a secure PIN - If an attacker steals your smartphone but cannot guess the PIN to access it, they can do no wrong. Therefore, it is critical that you have an unlock code on the lock screen and that the latter is complex enough (hence difficult to guess).
- To set the PIN on Android, go to Settings> Security> Screen Lock> PIN (or Settings> Security> Screen Lock> Pattern if you want to use a gesture instead of the numeric code).
- To set the PIN on the iPhone, go to Settings> Touch ID & Passcode> Change Passcode.
- Disable SMS display on the lock screen - another security measure you can take is to disable SMS notifications on the lock screen. This way, if an attacker tries to activate WhatsApp with your phone number and wants to see the verification code for the service, he will not be able to succeed.
- To disable SMS on Android lock screen, go to menu Settings> Security> Lock screen> PIN, set your PIN and choose to hide only sensitive content.
- To disable SMS on iPhone lock screen, go to Settings menu> Notifications> Messages and uncheck Show on "Lock screen" option.
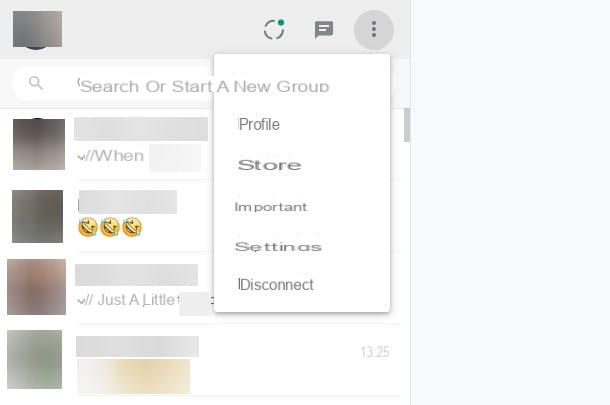
- Check your WhatsApp web sessions - as mentioned above, someone could try to steal your identity using WhatsApp Web. To avoid this risk, go to the Settings> WhatsApp Web menu in WhatsApp and check all active sessions in your account. If there are any suspicious ones, press the Disconnect button on all computers and the "spies" will lose the ability to access WhatsApp Web (as they will be prompted to scan the service's QR code again).
- Avoid public Wi-Fi networks - even if wireless network "tracking" is no longer as effective as it used to be, it's best to avoid public Wi-Fi networks. If you can, opt for your carrier's 3G / LTE network if you can.
- Listen to "mom's" advice - if you want to avoid someone poking their nose into your online conversations, listen to your mom's advice: don't lend your phone to strangers, don't leave your smartphone unattended for too long ... and don't be late at night! :)
- As some independent tests published online show, end-to-end encryption was initially applied only to the Android version of WhatsApp. On the other software platforms, an encryption system based on the RC4 algorithm was used, which is notoriously more vulnerable to attacks. Now, however, the situation should have changed, end-to-end encryption is slowly coming to all versions of WhatsApp. ︎