The problem of being vulnerable to external attacks does not depend so much on the skill of a potential hacker, it seems very unlikely that an expert hacker will waste time forcing a normal internet browser to enter the computer.
 Almost always, however, those who enter external computers are normal people who "try" and, using programs or small tools also available for free on the internet, launch a scan their subnet, to see if there are any unsecured connected computers.
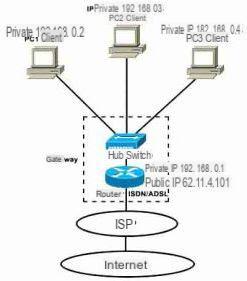
Almost always, however, those who enter external computers are normal people who "try" and, using programs or small tools also available for free on the internet, launch a scan their subnet, to see if there are any unsecured connected computers.A subnet or subnet is made up of computers connected to the same router. The router allows PCs to go out onto the internet and "routes" data packets from one PC to another. To understand the concept of subnet, you can think of an office whose computers are connected to each other and that go out to the internet with the same IP address, through the same router or gateway. The same thing happens at home with some providers such as Fastweb.
In another article the guide to create a corporate network at home or in the office and share folders and other resources.
In another article I described the best free programs to scan the network, such as Network Scanner.
These programs check if it is possible to access a PC via the Telnet, NetBios, Snmp, FTP service or the explorer on shared folders.
The Network Scanner program is very convenient because it does not require installation and can be carried around by copying it on a usb stick and use it on PCs so as not to be noticed. The main function is to see which computers are on and connected to the network in a subnet by doing the so-called "ping", it also scans the TCP ports and check any resources shared by that computer and then accessible without needing to know any administrator passwords. Finally, they list all the details available for each computer and therefore mac address, computer name, workgroup name, name of the user who is using it, and, if that pc has the snmp service active, lots of information on the hardware and software installed for a whole overview on that pc.
To search files on a LAN as if it were your own PC, you can use the program Lan Search Pro of which there is also the portable version and which becomes very useful to search among the computers on the network and their shared folders.
The program that verifies e show shared folders and visible of computers connected in a network is Find Shared Folders
The Range of IP addresses to be fed to these programs is formed in this way:
START -> Network connections -> Show all connections -> Right click on the active connection with the word connected -> Status -> Support -> Details
In Details the IP address is written, for example 192.168.0.5, the Gateway, for example 192.168.0.1.
The fact that the first three series of numbers are identical indicates a subnet made up of 255 (from 1 to 255) possible addresses that are attached to the same Router or Gateway and which therefore can freely exchange data unless a computer is present a firewall that isolates it from the subnet. If there is no firewall, the computer is at high risk of intrusion into the subnet. These IP addresses are internal, i.e. these computers do not go out on the internet with the address 192.168.XX.XX but with the same address that is assigned by the internet service provider and which coincides with the external external IP of the router.
In another article programs are reported to set a static and fixed IP with a click, memorizing and changing them easily.
Out that subnet therefore, to enter one of these PCs, you have to join a wifi network and capture network packets to spy on what is being done on the internet.
Later you could even bypass the router password if the default password is left, it is known for all routers on the market.
I was very simplistic to avoid concepts that are not intuitive and not easily understandable, the important thing is that the reader knows the risks of shared folders, of not having a firewall and how easy it is to get into a PC.
For those who want to try to scan the network and "spy" on the computers of others, it must be emphasized that there is no nothing illegal watching who leaves unprotected and even shared files and folders; it is illegal to try to crack passwords and routers.
For those who are intrigued and they want to know more about networks, on IP addresses, gateways, routers, subnets, etc. etc. I point out this excellent guide to networks.
Enter the PCs and see the shared folders of other computers