Given the numerous requests I have received in this regard, today I return to deal with a topic that I have already dealt with several times in the past: how to spy on whatsapp android. No, don't worry, I don't want to encourage illegal activities like monitoring electronic communications. Far from it. With today's tutorial I want to analyze some techniques adopted by cybercriminals to capture our conversations on WhatsApp and I want you to discover all the "weapons" we have at our disposal to defend ourselves.
Fortunately, the situation is not as dramatic as some want it to appear. On Android, WhatsApp uses an end-to-end named encryption technique that makes messages visible only to their respective senders and recipients. The chats arrive in encrypted form even on the servers of the service and it is difficult for an attacker to "capture" them with activities such as sniffing wireless networks (unless there is a flaw in the implementation of the encryption system, we cannot know this ). In any case, it is forbidden to let your guard down!
There are techniques - if we want less refined but equally very dangerous - that allow you to steal a person's identity on WhatsApp by physically accessing his smartphone. Let's see immediately what they are and let's equip ourselves to prevent someone from putting them into practice on our mobile phones.
Spy on WhatsApp Android with WhatsApp Web

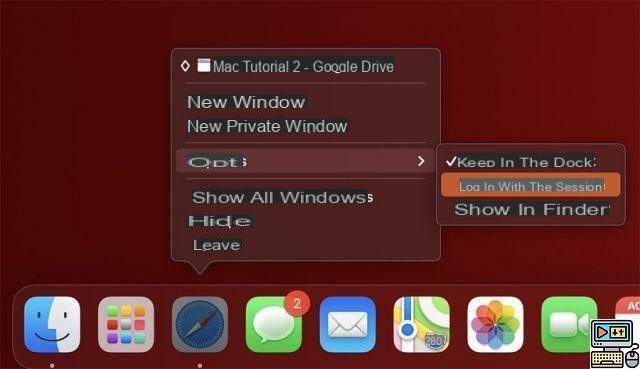
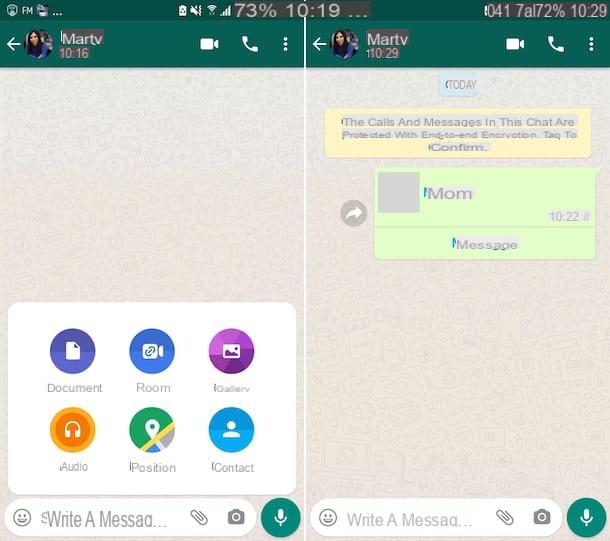
Web WhatsApp, as you surely know, is a WhatsApp function that allows you to access the service via the Web. It works on any computer and is compatible with many different browsers: Chrome, Firefox, Opera and Safari (with limited functions, as I also explained to you in my post on WhatsApp for PC).
Using it is really simple: just connect to the site web.whatsapp.com, scan the QR code that appears on the PC screen with the smartphone camera and that's it. So what's dangerous about all of this?
The risks for our privacy come from the fact that WhatsApp Web is able to store the user's identity (just put the check mark on the option Stay connected to access the service without having to scan the QR code) and the fact that the smartphone is not required to be on the same Wi-Fi network as the PC. WhatsApp Web works only if the smartphone on which WhatsApp is installed is switched on and connected to the Internet, but the connection can be made via any wireless network or even via the 3G / LTE data network, the two devices do not necessarily have to be in the same room.
This means that an attacker could steal your smartphone with an excuse (e.g. the need to make an urgent call), use it to access WhatsApp Web and maintain access to your conversations for several days.
How do you differ: to defend yourself against these types of threats you have to practice some common sense, so, for example, you don't have to lend your smartphone to strangers and you don't have to leave it unattended in public places.
An effective solution to defend against malicious people is certainly to activate a protection system on your device by biometric recognition (unlocking by face or using a fingerprint, for example). In this specific case, in fact, in order to confirm access to Web WhatsApp/desktop the authorization of the device owner is required. Otherwise, the connection to the service will be denied.
Finally, you can go to the menu Chat> […]> WhatsApp Web of WhatsApp and check all active WhatsApp Web sessions on your account. If you detect any suspicious activity, press the button Log out of all computers and all PCs connected to your account will lose access (you will need to scan the QR code again with your mobile phone to access WhatsApp Web).
Clone WhatsApp

Another of the techniques used by cybercriminals for spy on WhatsApp Android is to clone the MAC address of the victim's phone, install WhatsApp and steal the identity of the person to be spied on. This is a very elaborate procedure, quite long to put into practice, but still very dangerous.
The MAC address, if you have never heard of it, is a 12-digit code that allows you to uniquely identify all devices capable of connecting to the Internet. WhatsApp also uses it, along with the phone number, to verify the identity of its users… and this is where cybercriminals can get their hands on it.
There are applications, such as BusyBox e Mac address ghost, which allow you to disguise the MAC address of Android smartphones (only those previously subjected to the root procedure) making it look like that of another phone.
This "trick" can allow an attacker to clone the MAC address of a phone (the smartphone of the person to be spied on), install a new copy of WhatsApp, activate it with the victim's number and thus obtain full access to all his conversations.
How do you differ: this type of attack, like the one we saw earlier, requires physical access to the victim's smartphone. This means that you can avoid this by not leaving your phone at the mercy of strangers and by applying some basic protection measures.
One of these is definitely theuse of a secure PIN to avoid unauthorized access to the smartphone (on the other hand, to view the MAC address of the mobile phone just go to the settings menu, you must not be a hacker!). If you haven't already done so, set a secure PIN on your Android by going to the menu Settings> Security> Screen Lock and selecting the voice PIN from the latter. Alternatively you can also select the item Sequence and use a gesture (ie a "drawing" to be done with your finger on the phone screen) instead of the numeric code.
Another piece of advice I feel like giving you is that of prohibit the display of SMS in the Android lock screen (in this way, even the SMS with the WhatsApp verification code cannot be viewed by malicious people). To do this, go to the menu Settings> Security> Screen Lock of Android, set a PIN or a Sequence and choose to hide sensitive content.
Spy apps

As I also explained to you in my tutorial on how to spy on Android phones, the Google Play Store is full of applications for parental control and remote location of smartphones which, if properly configured, can allow an attacker to spy on a phone from a distance, capturing everything. what is typed on his keyboard and what happens on his screen.
How do you differ: even spy apps need physical access to the phone in order to be installed, so all the advice I gave you before applies. Also you could try to access the menu Settings> Apps> All of Android and see if there is any "suspicious" name among the applications installed on the phone.
Unfortunately, the absence of “suspicious” names from the Android menus does not completely dispel the doubt concerning the presence of spy applications on the mobile phone. This kind of app, in fact, has the ability to hide itself from all the system menus and to get rid of it you must first unlock them by entering the appropriate passwords.
The spied person obviously does not know these passwords and therefore can get rid of the spy application only by formatting their device. If you have this kind of suspicion but you have not found "strange" names in the Android menu, try to reset Android following my tutorial on the subject and you should solve the problem.
Wireless sniffing

WhatsApp for Android, as stated at the beginning of this post, uses an end-to-end encryption system called TextSecure. This system is based on the use of two keys: a public key which is shared with our interlocutor and serves to encrypt outgoing messages and a public key which instead resides only on our smartphone and allows us to decrypt incoming messages.
With end-to-end encryption, the risk associated with monitoring wireless networks (so-called wireless sniffing) is minimized, as all information circulates in encrypted form but… there is a but.
WhatsApp is a closed source application, we cannot thoroughly analyze its source code, and therefore we cannot know if the encryption is always applied, if in some countries it is deactivated at the request of local governments or if its implementation has been made to rule of art. It goes without saying that a simple mistake in using this technology would make the application vulnerable again and greatly lower the security of our conversations.
A first alarm bell about the security of end-to-end encryption in WhatsApp came in April 2015, when a team of German researchers discovered that only Android> Android communications were protected with TextSecure encryption. In other circumstances the app used a technology based on the RC4 algorithm which is no longer believed to be impenetrable and is much easier for cybercriminals to decode.
The situation should now be improved. The developers of the WhatsApp encryption system have ensured that end-to-end encryption will gradually arrive on all platforms, but the unknown is the impossibility of checking the WhatsApp code. We cannot know if and what types of communications are actually encrypted. We must "trust".
How do you differ: if end-to-end encryption doesn't work, unfortunately we users can't do anything. The only advice I can give you is to avoid public Wi-Fi connections, which are known to be the favorite hunting ground for cybercriminals. For the rest, if you do not trust WhatsApp, stop using it and contact another messaging application with end-to-end encryption, possibly open source (in order to have more guarantees on the functioning of the encryption).