Summary
Tracking Systems PIN Code Passwords Double Authentication Data Backup Updates Antivirus VPN Tracker Blocker Firewall Root and Jailbreak Hacked Apps ReviewsLet's face it, few of us have the right safety reflexes. However, our smartphones, our tablets and our PCs house a great deal of private data. It is therefore in your interest to follow these basic and important rules.

Through several essential questions, we give you advice and tools to better secure your devices and protect your personal data, whether on PC, smartphone, tablet, Android or iOS. Very practical tips as a good resolution for this beginning of the year 2021, in order to use your devices as quietly as possible
Be more vigilant when telecommuting
Since the coronavirus crisis began in the middle of March 2020, our habits have changed to protect the population from the coronavirus. Teleworking is thus strongly encouraged for the millions of workers who have the possibility of working from home.. Teleworking requires you to be even more vigilant because you will be handling professional data.
Here are a few tips :
- Separate personal and professional work environments by creating a new session on your computer;
- Update the anti-virus;
- Use a secure VPN if you are handling sensitive data,
- Encrypt your devices if possible.
How to activate location systems on iPhone, iPad, AirPods, Apple Watch, Android and Windows 10?
Google, Microsoft and Apple offer tracking systems to find your lost devices. This still requires your devices to be turned on and connected to a network. Otherwise, you retrieve their last location.
Android
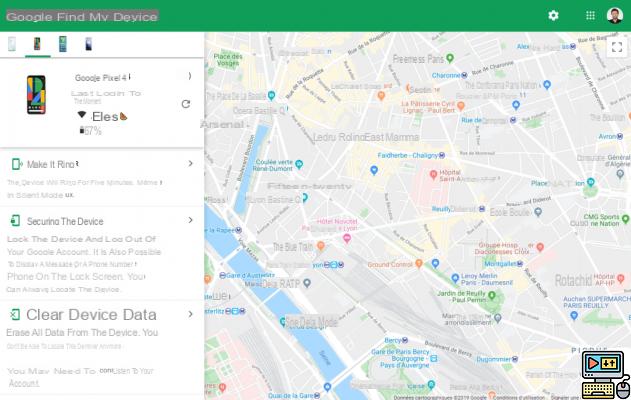
The Find My Google Device feature isn't the only such solution, but it is one of the most effective. It provides access to the following tasks: be able to display the location of your device, ring a lost device, lock it or erase its data.
To use it, go to google.com/android/find to locate all of your Android devices that have been set up with your Google account.
iPhone, iPad, Mac, AirPods et Apple Watch
At Apple, the Find My application allows, as its sound suggests, to locate all Apple devices, including an Apple Watch or Apple AirPods Pro. Like the Google function, you can also view the location of your devices at icloud.com/find.
Microsoft Windows 10
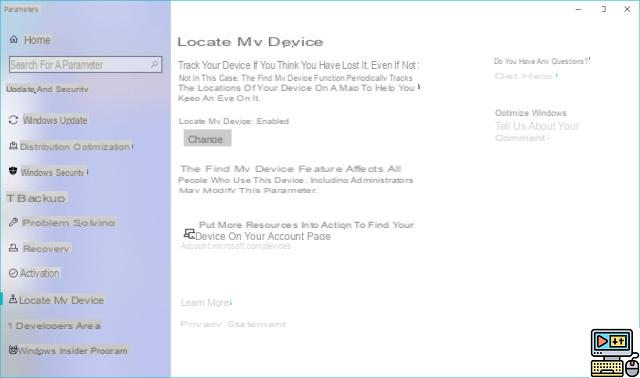
For Windows 10, Microsoft has also set up a similar tool that you will find at this address: account.microsoft.com/devices. Remember to activate this option on your device to take advantage of it.
Why personalize your PIN code and activate your device lock?
Another basic rule, changing the PIN code. Many of us still leave the default code, ie 0000 or 1234. Similarly, avoid very simple codes, such as 3579. More than 700 smartphones are stolen on average in Spain per year. You have every interest in making it more difficult for potential thieves.
Finally, lock your smartphone, with a diagram for example or by fingerprints. It's just common sense if you don't want other people to access your content. Afterwards, a diagram (template) may seem practical, but it is not as secure as a 6-character PIN code, a strong password or a fingerprint.
Note that these tips are also valid on iOS, and therefore iPhone, but also on any device, including a PC running Windows 10.
How to create and manage your passwords?
This is advice as old as the Internet. It is important to use complex and different passwords. Numerama has created a file to explain how to create a complex and memorable word.
One of our tips is to use a password manager that can generate complex passwords, store them securely and automatically connect you to certain services.
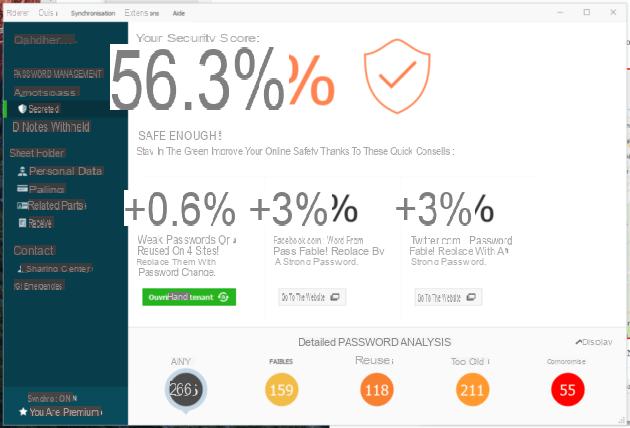
Dashlane interface
The whole problem therefore lies in choosing the ideal solution to adopt, because the offers are numerous and all have advantages and disadvantages. We recommend 1password, LastPass or even Dashlane. You also have Bitwarden which is open-source and free. You can also use these solutions to encrypt your notes and documents.
LEARN MORE
KeePass: How to use the open-source password manager? - Tutorial
We have written a comparison of the different password manager solutions.
Why is it necessary to enable two-factor authentication?
Double authentication has become essential to properly secure accounts containing personal and professional data, such as Google, Facebook, Apple, Microsoft, Amazon or PayPal.
To learn more
Double authentication (2FA): why and how to secure your Google, Facebook, iCloud, Steam accounts ...
Unfortunately, it is little used when it is not compulsory. This is because it is often restrictive for users. Yet it is one of the most effective ways to secure your accounts and services.
It adds, in addition to the password, a new authentication step, such as a message with a code, the use of a security key or an authentication application. If someone tries to access your account after having hacked your password, then they should normally be blocked by the confirmation of your identity, which will take place on your smartphone.
We will help you: we have grouped the direct links to activate double authentication on all the main services.
How to save your data?
It's still basic, but too many of us don't back up our data: contact lists, but also photos for example. We have listed a number of backup solutions, which you can find at this address.
On iOS and iPadOS, you can enable iCloud backup, which is very efficient. We also advise you to double the backup of your photos through Google Photos or Amazon Photos.

Google Photos
Download Google Photos Free APK
Amazon Photos
Download Amazon Photos Free APKMore generally, you can use cloud services or simply back up your data on physical media.
To learn more
USB-C portable external SSD comparison for Android, Windows and macOS
We have published a buying guide dedicated to storage media, but also a comparison of the best external SSDs: they are compact, light and relatively accessible.
Do you have to encrypt your data?
All OSes allow stored data to be encrypted, it is an effective way to protect your data, but it is not the only one. Apple introduced the default encryption since iOS 8, while it was imposed by Google on Android Marshmallow (but available since version 3.0 Honeycomb of the OS). Obviously, this is also the case on Windows 10 and macOS.
Encryption is a process of protecting your data with a unique key, so as to make them illegible by a third party. By analogy, we can see encryption as a safe in which is located all the data that we want to keep confidential. Access to its content de facto requires the key to the safe. Encryption is not tamper-proof, but, if used properly, can be strong enough to deter anyone attempting to break it.
Numerama has dedicated a file to encryption on Android and iOS. The algorithm used by Apple's encryption engine is AES 256 (for Advanced Encryption Standard). On Android, it depends on the manufacturers, they can use different methods depending on the version of the OS but also on the components of the smartphone.
We therefore strongly recommend that you activate encryption, but be aware that this will have a fairly limited impact on the performance of your device. Personally, I have disabled encryption on macOS because I don't store sensitive files on it.
Why is it important to keep your devices up to date?
Things have changed a lot in 10 to 15 years in IT. Whether on Windows 10, macOS, iPadOS, iOS, Android, Chrome OS ... Updates are more frequent and often include small fixes and security updates. On Android, Google also deploys updates dedicated to security on a monthly basis.
Hackers often take advantage of outdated software or device to exploit a security vulnerability.
It is therefore important to keep your OS, your applications and your connected objects up to date.. Basically anything that can be updated. We therefore advise you toactivate automatic update systems (apps and system) which exist on all modern OS today.
Do we have to install an antivirus?
Antiviruses are unnecessary on Android, Mac, iPad and iPhone
Hardly a week goes by without a security company reporting the presence of malware on Android. More often, these reports and other studies come with some reminders that (precisely) the security solution (of the person who commissioned the study) is useful and recommended. However, Android is - by its very nature - more secure than a desktop computer. You don't need any antivirus or anti-malware, especially if you follow the tips above.
First, Google's platform has the ability to detect known malware when downloading an app, but also afterwards. Google is also working to deploy fixes using Google Play Services, without having to update your system.
More generally, Android has built-in security features that dramatically reduce the frequency and impact of app security issues. The system is designed for developers to build their apps with the default system and file permissions and avoid potential security concerns. Moreover, it is this authorization system that limits the effectiveness of antivirus and other anti-malware. CQFD.
On the other hand, one of the advantages of these solutions, and that we cannot take away from them, is that they put forward most of the basic rules of this article, and in a personalized way. Which is a good thing in itself. But don't forget that security is not so much a matter of software as of behavior, and it is up to you to adopt the tools that we indicate to protect yourself from the various risks mentioned.
On iPhone, Mac or iPad, it's the same, you don't have to do anything except follow the advice in this file.
Do you still need to install an antivirus on Windows 10?
You probably remember the days of Windows XP: it was totally inconceivable and unconscious to wander the Web without antivirus. Things haven't changed much on Windows 10, with one exception. Microsoft's OS includes its own antivirus called Windows Defendsr. There are alternatives, some are worth it, but Microsoft's native tool is now efficient enough not to bother installing a third-party solution.
For Windows 10, we therefore recommend that you activate Windows Defender.
Are VPNs Necessary to Secure Your Devices?
There are two main advantages to the use of a VPN by individuals: bypass geographic filtering by using an IP address from another country via a VPN, and better protect your anonymity on networks by masking its real IP address and encrypting the information sent.
The VPN does not in itself constitute absolute protection - moreover, absolute protection does not exist -, but it is an easy technique to set up and which improves the confidentiality of data exchanged on the web, particularly on public networks.
The choice of your VPN will therefore depend a lot on the use you want to make of it. If you want to access the Disney + catalog, you will look for a powerful VPN, at the risk that it protects your data less. On the other hand, if you travel to a country in which the web is censored and where certain uses are prohibited, you will go to a VPN that does not record your traffic and that will not give your information to governments ... even if it means surfing a a little slower.
We advise you to consult our comparison of the best VPNs.
How do you know which sites have information about you?
Even if, since 2018, websites have been required to obtain consent from Internet users regarding the cookies installed on their computer, it may be practical to use a tracker blocker to prevent other services from having information about self.
Concretely, these blockers allow you to analyze all third-party sites that collect information about you when you browse another website. These are often traffic analysis tools, such as Google Analytics, but they can also be advertising analysis tools or other third-party sites whose plug-ins have been installed by the publisher. of the website. These trackers are overwhelmingly harmless, but they can be annoying if your privacy is particularly important.
In the matter, the reference is called Ghostery and is available both on PC and on iOS or Android smartphones or tablets. However, the behavior of the service is very different from one platform to another.
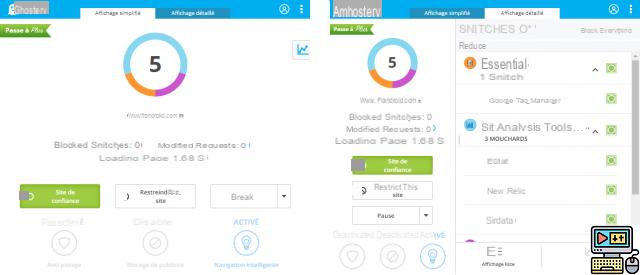
The Chrome Ghostery extension for computers
On the computer, Ghostery is a simple extension for Google Chrome and Mozilla Firefox browsers. Once the extension is installed on your browser, it will allow you, free of charge, to view the trackers present on a particular website, as well as their nature: essential, advertising, unidentified or site analysis, for example. You can then choose to block them individually if you wish. In addition, for users who wish, Ghostery allows you to choose to trust or globally restrict a website to activate or block all trackers. Ghostery also offers an ad blocker by default, which can be easily disabled if you want to support a particular website.

Ghostery
Download Ghostery Free APKOn smartphone, Ghostery presents himself this time in the form of an application or, more precisely, an Internet browser. It actually uses the source code of Firefox on smartphones, but adds all the functions related to the protection of privacy that can be found on the Chrome and Firefox extensions on PC. The application uses the general principle of a browser, but, by clicking on the ghost logo to the left of the address bar, it is possible to access tracker data, with the same options as on the extensions for PC. Ghostery does not, however, offer control over the trackers used by other applications installed on your smartphone.
Should you use a firewall?
Firewall or firewall, there was a time when it was necessary to install firewall software on Windows, which was a user's first line of defense against threats from the Internet.
The firewall is a piece of equipment or an application that filters outgoing and incoming connections. which are carried out to and from your computer. The firewall is located between the user and his applications on one side and the Internet connection on the other.
Windows Defender Firewall
You may not know it, but you are already protected by a firewall, that of your box. And very often, a second, that of your Windows 10 PC. We therefore advise you to activate the firewall on your Windows 10 PC to increase the security of your machine. The firewall is therefore important, but not essential.
On Android and iOS, both OS already have options to limit internet access to applications. It is already a sufficient security tool.
Can you root or jailbreak your smartphone?
Root or jailbreak your device is to take the risk of leaving doors open. This is because those two words ultimately mean the same thing: getting some very advanced permissions to access your system that you don't necessarily need.
To learn more
Is rooting on Android doomed to disappear?
This allows you, optionally, to install certain features, but it is no longer as useful and it is especially not recommended to do so. Our advice: avoid getting into it, especially if you don't know what you're doing.

What are the risks of downloading apps and games from unknown sources?
We're not going to lecture you, if you want to download, do it. Another day we will talk about the economy behind mobile applications and games, and especially the independents and other studios that make a living from them. If we recommend that you avoid downloading pirated apps anywhere, it's simply because they often contain malicious code.
To learn more
How to install an APK file on an Android smartphone or tablet?
Overall, Avoid downloading APKs outside of the Play Store and from an external source unless you are completely sure of the origin of the file. Indeed, these files can be corrupted. If, however, you don't want or can't go through the Google store, take a look at our list of the best alternatives to the Play Store.
The advice is the same for macOS and Windows 10: avoid downloading programs or games from unknown sources. For iOS and iPadOS, Apple has further locked its system, it is very difficult to do without the App Store to download an application.